I am an tenured track assistant professor at the department of computer science at New Jersey Institute of Technology (NJIT). Before joining NJIT, I received my Ph.D. degree from Rutgers University, where I was advised by Dr. Yingying Chen. My research interests span Applied Machine Learning, Security and Privacy for Mobile Systems, and Robust and Trustworthy ML/AI. My research work has been published at top-tier security, mobile sensing, and ML/AI venues (e.g., IEEE S&P, ACM CCS, ACSAC, ACM MobiCom, ACM MobiSys, ACM SenSys, ACM MobiHoc, ACM UbiComp, ICCV, AAAI, ECCV).
News
- Mar. 2024: We have two papers accepted by ACM MobiCom 2024. Our work is on inaudible backdoor attack via frequency trigger injection and the other work is on practical adversarial attack on WiFi sensing.
- Aug. 2023: We have two papers accepted by ACM CCS 2023. One work is on speech evaesdropping via Phased-MIMO mmWave Radar and the other work is on mining vital sign embedded sensitive info via AR/VR (Acceptance rate: 19%)
- May 2023: Dr. Shi has been selected as an honoree for 2023 Rutgers ECE Graduate Academic Achievement Award.
- May 2023: Our work on vital sign monitoring via AR/VR headsets has been accepted to ACM MobiSys 2023.
- Apr. 2023: Our work on privacy leakage via unrestricted AR/VR motion-position sensors has been accepted to IEEE S&P 2023.
- Apr. 2023: Our work on revealing emotions with smartphone sensors has been accepted to IEEE ICDCS 2023. (Acceptance rate: 18%)
- Feb. 2023: Our work on Out-of-Sight Clean Voice Command Attacks has been accepted to ACM WiSec 2023. (Acceptance rate: 18%)
- Sept. 2022: Our work on exploring stastical assessment for robust WiFi sensing has been accepted to ACM SenSys 2022. (Acceptance rate: 24%)
- June 2022: Our work on backdoor attack against compact DNN has been accepted to Springer ECCV 2022. (Acceptance rate: 28%)
- June 2022: Our work on audio-domain backdoor attack via unnoticeable triggers has been accepted to ACM MobiCom 2022. (Acceptance rate: 19%)
- May 2022: Our work on defending spoofing voice attacks via cross-domain learning has been accepted to IEEE ICDCS 2022. (Acceptance rate: 19%)
- Aug. 2021: Our work on detecting machine-induced audio attacks via microphone array has been accepted to ACM CCS 2021. (Acceptance rate: 18%)
- Aug. 2021: Our work of learning private voice information from AR/VR headsets has been accepted to ACM MobiCom 2021. (Acceptance rate: 17%)
- Aug. 2020: Our work on training-free voice authentication via cross-domain comparison has been accepted to ACSAC 2020. (Acceptance rate: 17%)
Recent Research Work
My current research focuses on designing machine learning and sensing solutions to address real-world problems, including user authentication, 3D skeleton posture reconstruction, smart healthcare (e.g., examining the risk of COVID-19), indoor localization, activity/gesture recognition, etc. I am also interested in revealing security vulnerabilities in emerging machine learning/artificial intelligence (ML/AI), augmented reality/virtual reality (AR/VR), and voice assistant platforms, with the hope of addressing the inherited security issues and bringing trustworthiness to end users.
|
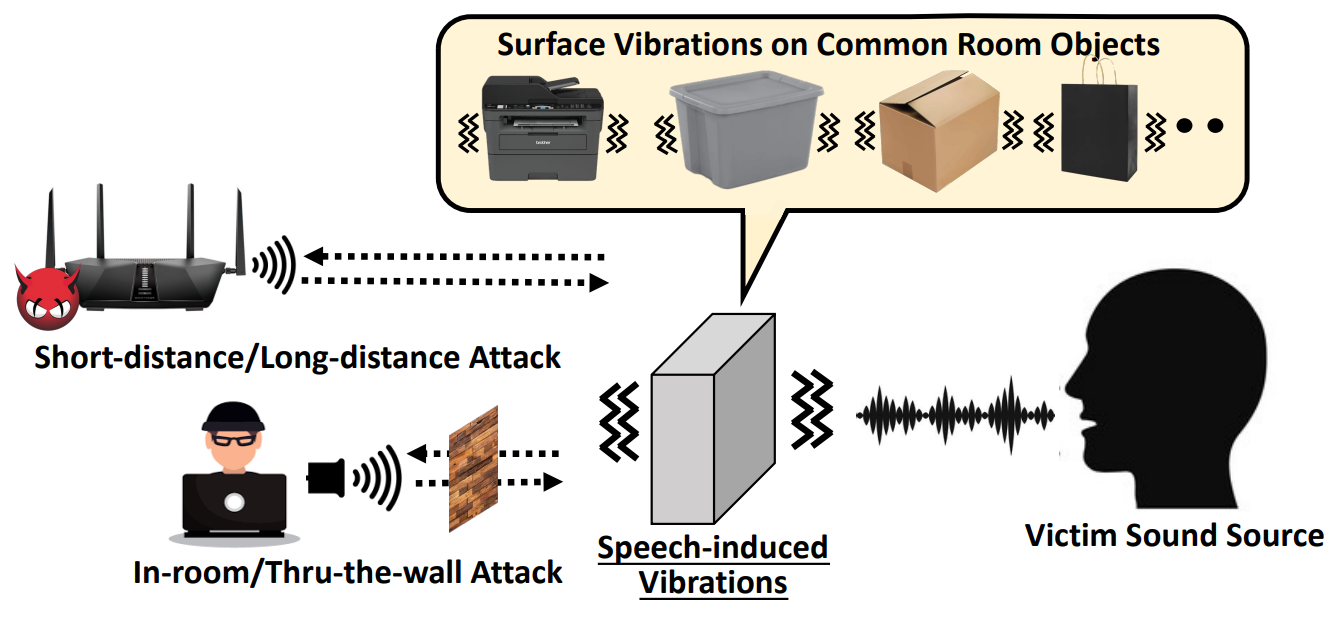
Privacy Leakage via Speech-induced Vibrations on Room Objects through Remote Sensing
[ACM CCS 2023] ACM Conference on Computer and Communications Security
We revisit the problem of speech eavesdropping and show that a remote, long-distance, and even thru-the-wall speech eavesdropping attack is possible. We discover a new form of speech eavesdropping attack that remotely elicits speech from minute surface vibrations upon common room objects (e.g., paper bags, plastic storage bin) via mmWave sensing, signal processing, and advanced deep learning techniques. |
|
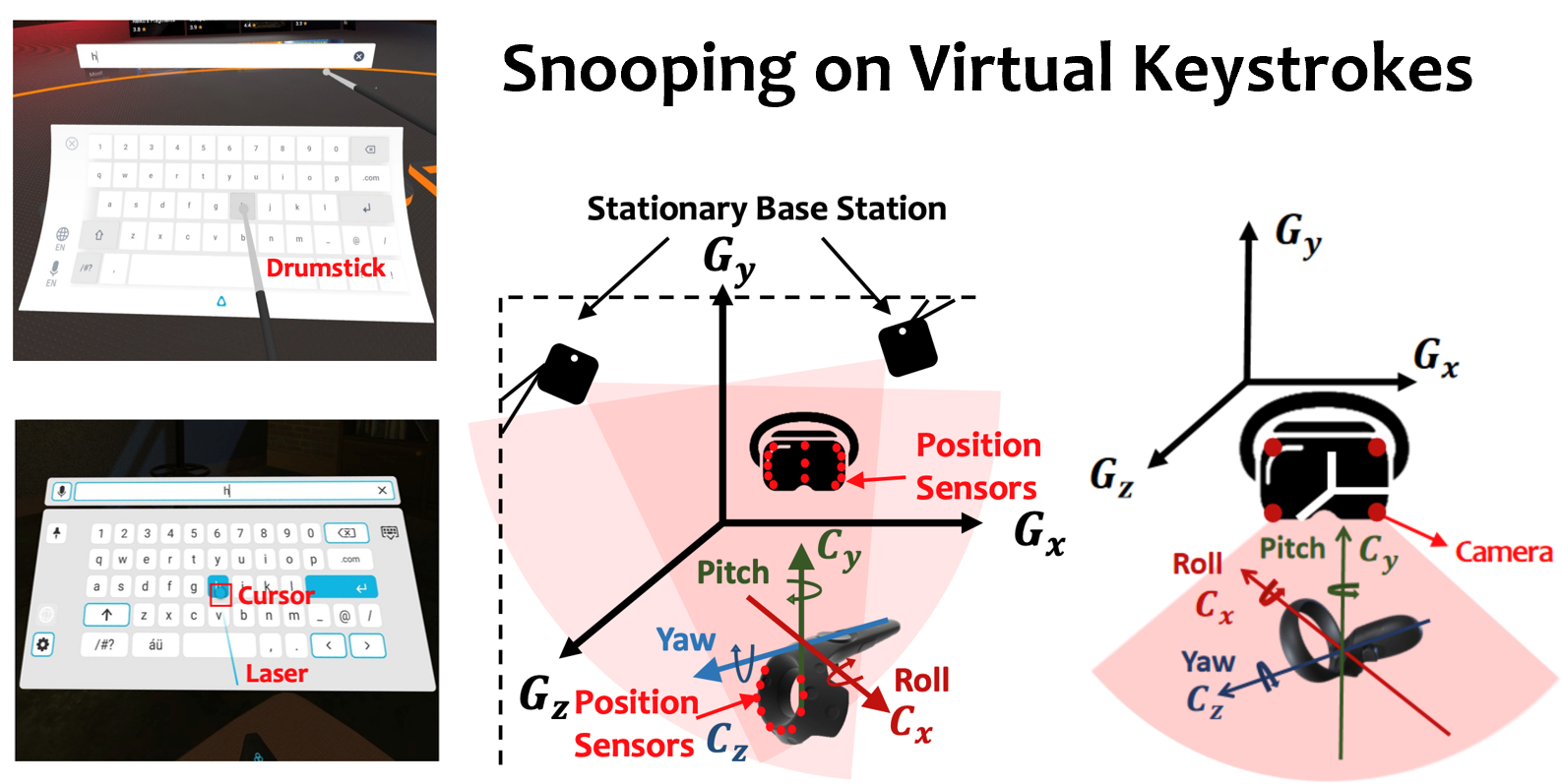
Privacy Leakage via Unrestricted Motion-Position Sensors in the Age of Virtual Reality
[IEEE S&P 2023] IEEE Symposium on Security and Privacy
PDF / Demo Video Virtual Reality (VR) has gained popularity in numerous fields. In this project, we conduct a comprehensive study to assess the trustworthiness of the embedded sensors on VR, which embed various forms of sensitive data that may put users' privacy at risk. We find that accessing most on-board sensors (e.g., motion, position, and button sensors) on VR SDKs/APIs requires no usecurity permission, exposing a huge attack surface for an adversary to steal the user’s privacy. |
|
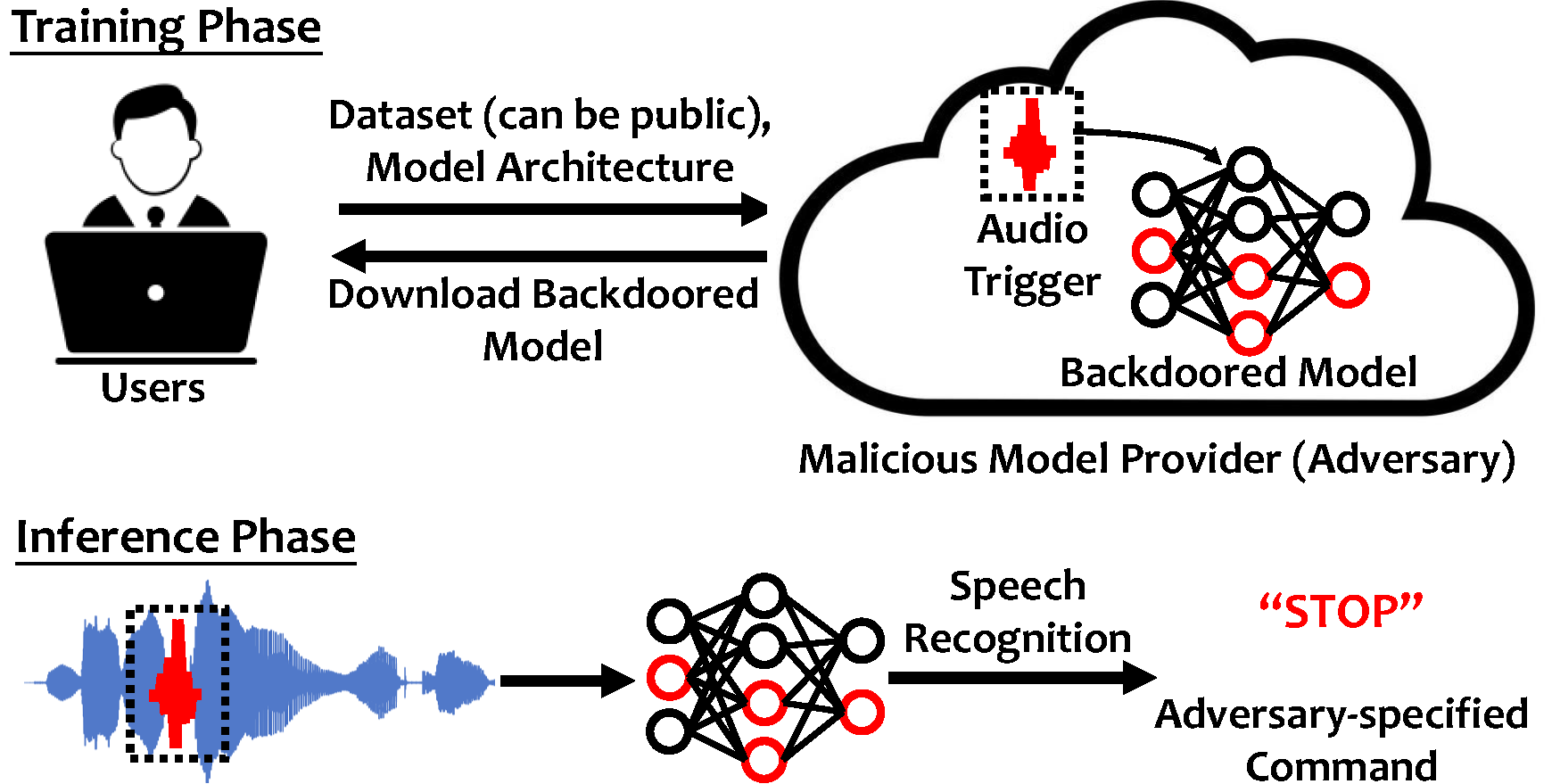
Audio-domain Position-independent Backdoor Attack via Unnoticeable Triggers
[ACM MobiCom 2022] Annual International Conference on Mobile Computing and Networking
Deep learning models have become key enablers of voice user interfaces. We investigate an effective yet stealthy training-phase (backdoor) attack in the audio domain, where hidden/unnoticeable trigger patterns are injected through training set poisoning and overwrite the model's predictions in the inference phase. An attacker can play an unnoticeable audio trigger (e.g., bird chirps, foot steps) into live speech of a victim to launch the attack. |
|
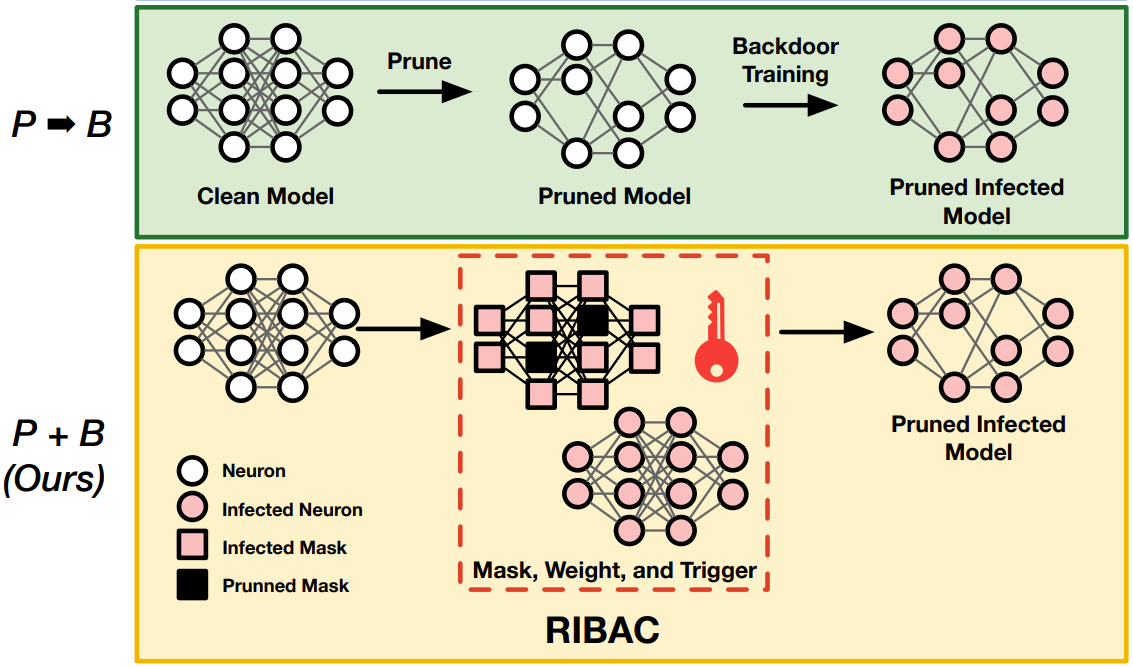
Robust and Imperceptible Backdoor Attack against Compact DNN
[Springer ECCV 2022] European Conference on Computer Vision
PDF / Code Recently backdoor attack has become an emerging threat to the security of deep neural network (DNN) models. In this project, we propose to study and develop Robust and Imperceptible Backdoor Attack against Compact DNN models (RIBAC). By performing systematic analysis and exploration on the important design knobs, we propose a framework that can learn the proper trigger patterns, model parameters and pruning masks in an efficient way. |
|
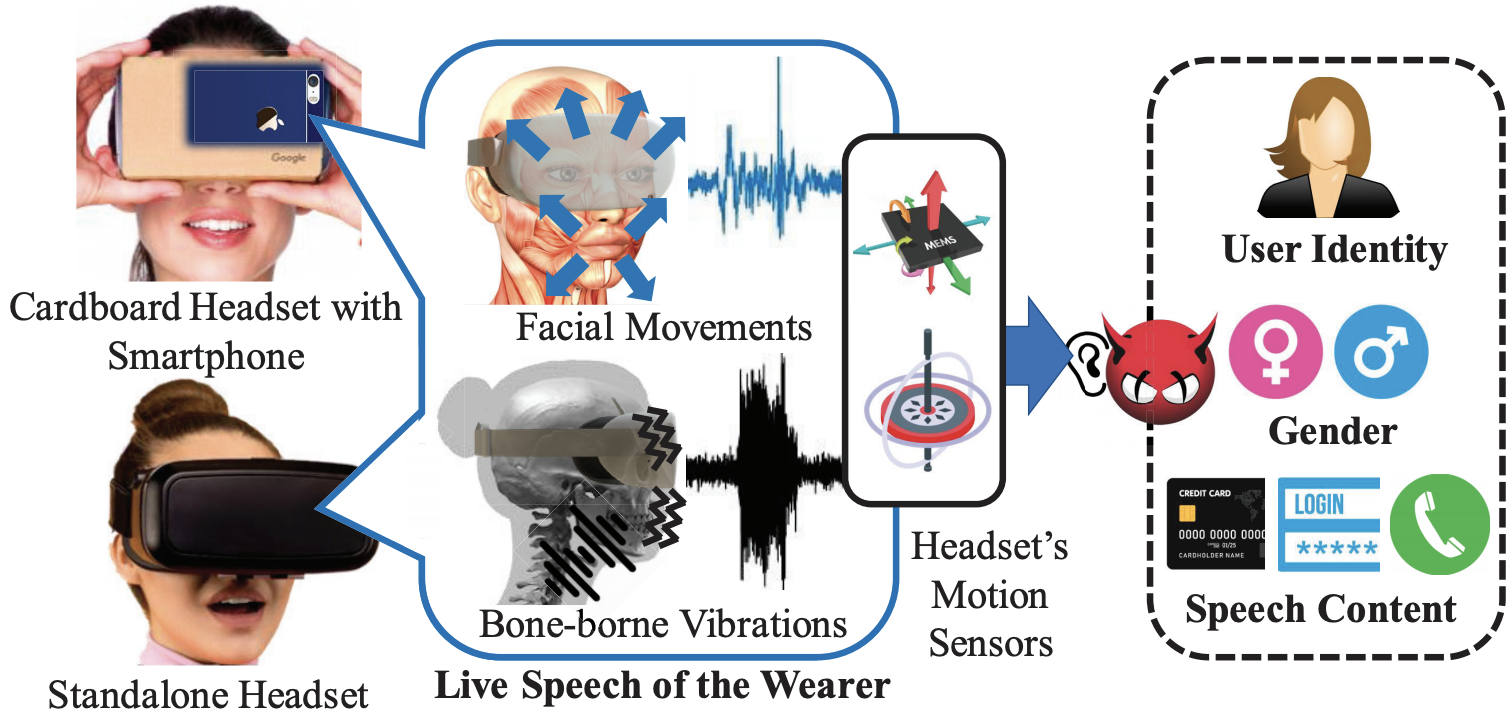
Privacy Leakage via Subtle Facial Dynamics Captured by AR/VR Headsets
[ACM MobiCom 2021] Annual International Conference on Mobile Computing and Networking
PDF / Demo Video We show a serious privacy risk of using voice interfaces while the user is wearing the face-mounted AR/VR devices. We design an eavesdropping attack, Face-Mic, which learns speech-associated subtle facial dynamics captured by zero-permission motion sensors in AR/VR headsets to infer highly sensitive information of live human speech. |
|
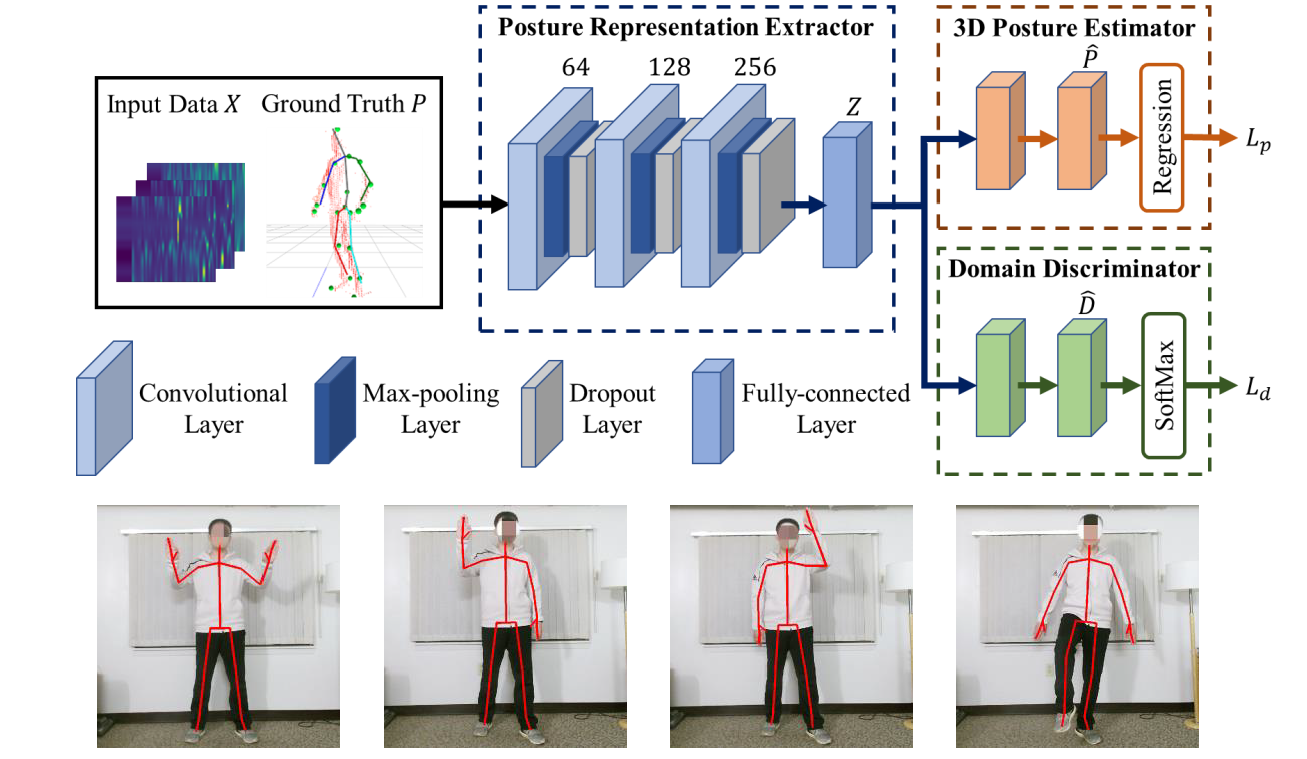
3D Skeleton Posture Reconstruction Leveraging mmWave Radar
[Elsevier Smart Health]
Human skeleton posture reconstruction is an essential component for human-computer interactions (HCI) in various application domains. Traditional approaches usually rely on either cameras or on-body sensors, which induce privacy concerns or inconvenient practical setups. This project proposes a low-cost contactless skeleton posture reconstruction system, mPose, which can reconstruct a user’s 3D skeleton postures by learning on 3D cloud points collected with a single mmWave radar. |
|
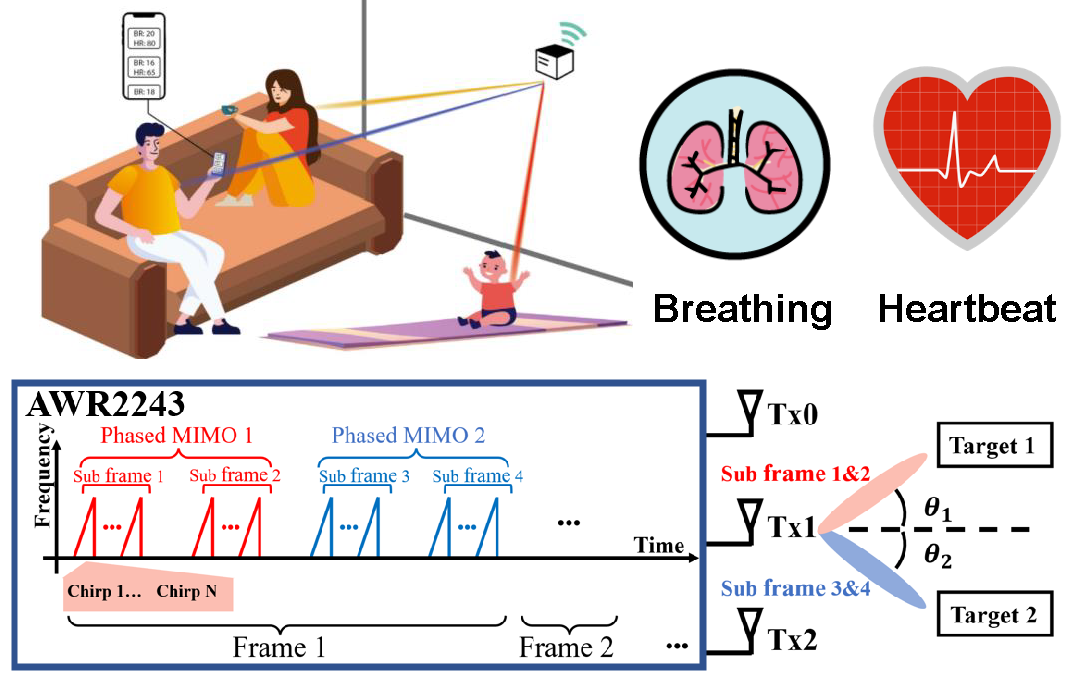
Monitoring Vital Signs of Multiple People Leveraging a Single Phased-MIMO Radar
[IEEE J-ERM] IEEE Journal of Electromagnetics RF and Microwaves in Medicine and Biology
Vital sign monitoring plays a critical role in tracking the physiological state of people and enabling various healthrelated applications (e.g., recommending a change of lifestyle, examining the risk of COVID-19). Traditional approaches rely on hospitalization or body-attached instruments, which are costly and intrusive. In this paper, using an off-the-shelf Texas Instrument automotive FMCW radar, we design and implement a time-division multiplexing (TDM) phased-MIMO radar sensing system that allows high-precision vital sign monitoring of multiple people. |
|
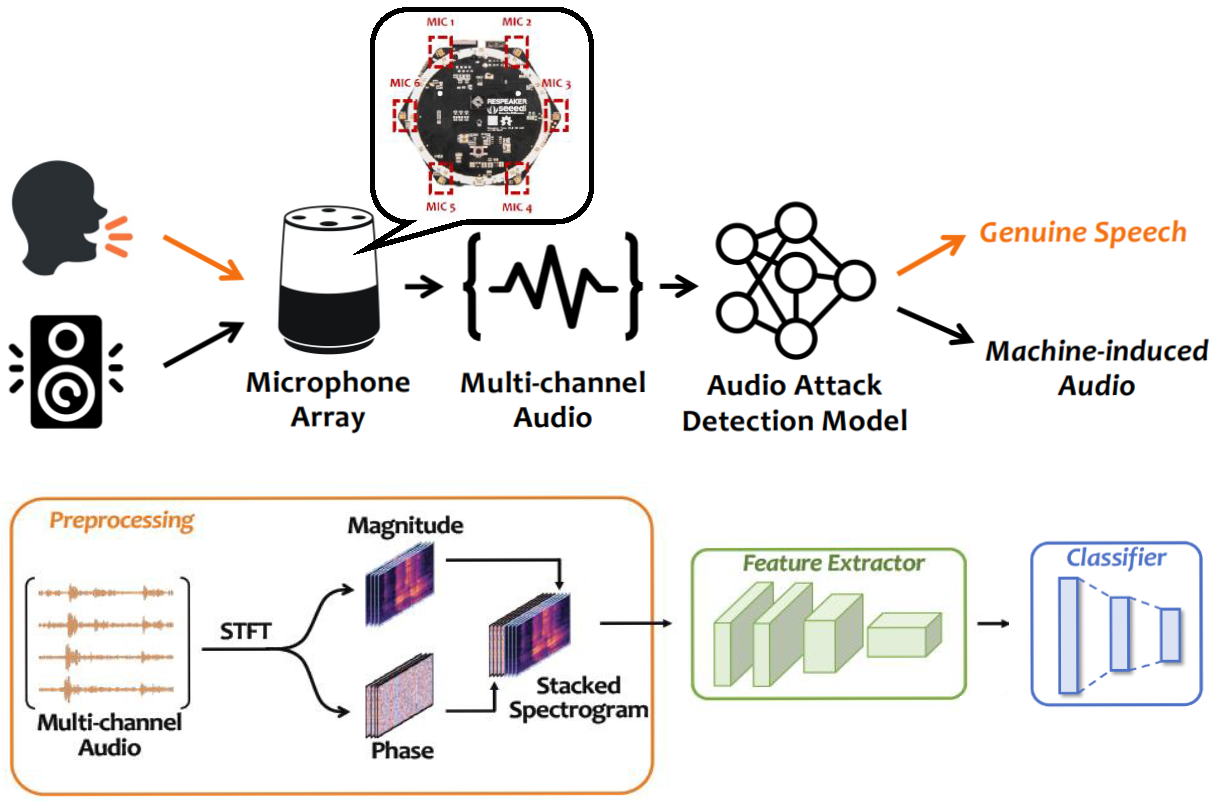
Detecting Machine-induced Audio Attacks with Microphone Array
[ACM CCS 2021] ACM SIGSAC Conference on Computer and Communications Security
With the popularity of intelligent audio systems in recent years, their vulnerabilities have become an increasing public concern. Existing studies have designed a set of machine-induced audio attacks1, such as replay attacks, synthesis attacks, hidden voice commands, inaudible attacks, and audio adversarial examples. This project builds a holistic solution for detecting machine-induced audio attacks leveraging multi-channel microphone arrays and learning spatial information in speeches via deep neural networks. |
Honors and Awards
- Rutgers ECE Graduate Academic Achievement Award
- Rutgers ECE Student Development Award
- ACM MobiCom Travel Grant
- Cisco sponsored Graduate Assistantship
- IEEE/ACM CHASE Travel Grant
- Siemens sponsored Graduate Assistantship
Conference Publications
Clean & Compact: Efficient Data-Free Backdoor Defense with Model Compactness,
Huy Phan, Jinqi Xiao, Yang Sui, Tianfang Zhang, Cong Shi, Yan Wang, Yingying Chen, Bo Yuan,
Proceedings of the European Conference on Computer Vision (Springer ECCV 2024).
SAFARI: Speech-Associated Facial Authentication for AR/VR Settings via Robust VIbration Signatures,
Tianfang Zhang, Qiufan Ji, Zhengkun Ye, Md Mojibur Rahman Redoy Akanda, Ahmed Tanvir Mahdad, Cong Shi, Yan Wang, Nitesh Saxena, Yingying Chen,
Proceedings of the ACM Conference on Computer and Communications Security (ACM CCS 2024).
Inaudible Backdoor Attack via Stealthy Frequency Trigger Injection in Audio Spectrogram,
Tianfang Zhang, Huy Phan, Zijie Tang, Cong Shi, Yan Wang, Bo Yuan, Yingying Chen,
Proceedings of the 30th Annual International Conference On Mobile Computing And Networking (ACM MobiCom 2024).
Practical Adversarial Attack on WiFi Sensing Through Unnoticeable Communication Packet Perturbation,
Changming Li, Mingjing Xu, Yicong Du, Limin Liu, Cong Shi, Yan Wang, Hongbo Liu, Yingying Chen,
Proceedings of the 30th Annual International Conference On Mobile Computing And Networking (ACM MobiCom 2024).
Privacy Leakage via Speech-induced Vibrations on Room Objects through Remote Sensing based on Phased-MIMO,
Cong Shi, Tianfang Zhang, Zhaoyi Xu, Shuping Li, Donglin Gao, Changming Li, Athina Petropulu, Chung-Tse Michael Wu, Yingying Chen,
Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (ACM CCS 2023).
FaceReader: Unobtrusively Mining Vital Signs and Vital Sign Embedded Sensitive Info via AR/VR Motion Sensors,
Tianfang Zhang, Zhengkun Ye, Ahmed Tanvir Mahdad, Md Mojibur Rahman Redoy Akanda, Cong Shi, Yan Wang, Nitesh Saxena, Yingying Chen,
Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (ACM CCS 2023).
Benchmarking and Analyzing Robust Point Cloud Recognition: Bag of Tricks for Defending Adversarial Examples,
Qiufan Ji, Wang Lin, Cong Shi, Shengshan Hu, Yingying Chen, Lichao Sun,
Proceedings of the International Conference on Computer Vision (ICCV 2023).
Privacy Leakage via Unrestricted Motion-Position Sensors in the Age of Virtual Reality: A Study of Snooping Typed Input on Virtual Keyboards,
Yi Wu, Cong Shi, Tianfang Zhang, Payton Walker, Jian Liu, Nitesh Saxena, Yingying Chen,
Proceedings of IEEE Symposium on Security and Privacy (IEEE S&P 2023).
Passive Vital Sign Monitoring via Facial Vibrations Leveraging AR/VR Headsets,
Tianfang Zhang, Cong Shi, Payton Walker, Zhengkun Ye, Yan Wang, Nitesh Saxena, Yingying Chen,
Proceedings of ACM International Conference on Mobile Systems, Applications, and Services (ACM MobiSys 2023).
EmoLeak: Smartphone Motions Reveal Emotions,
Ahmed Tanvir Mahdad, Cong Shi, Zhengkun Ye, Tianming Zhao, Yan Wang, Yingying Chen and Nitesh Saxena,
Proceedings of IEEE International Conference on Distributed Computing Systems (IEEE ICDCS 2023) (Acceptance rate: 18.9%).
Stealthy Backdoor Attack on RF Signal Classification,
Tianming Zhao, Zijie Tang, Tianfang Zhang, Huy Phan Phan, Cong Shi, Bo Yuan, Yingying Chen,
Proceedings of International Conference on Computer Communications and Networks (IEEE ICCCN 2023).
Out-of-Sight Clean Voice Command Injection Attacks through Physical Barriers,
Payton Walker, Tianfang Zhang, Cong Shi, Nitesh Saxena, Yingying Chen,
Proceedings of ACM Conference on Security and Privacy in Wireless and Mobile Networks (ACM WiSec 2023) (Acceptance rate: 18.5%).
Solving the WiFi Sensing Dilemma in Reality Leveraging Conformal Prediction,
Kailong Wang, Cong Shi, Jerry Cheng, Yan Wang, Minge Xie, Yingying Chen,
Proceedings of the ACM Conference on Embedded Networked Sensor Systems (ACM SenSys 2022) (Acceptance rate: 24.8%).
RIBAC: Towards Robust and Imperceptible Backdoor Attack against Compact DNN,
Huy Phan, Cong Shi, Yi Xie, Tianfang Zhang, Zhuohang Li, Tianming Zhao, Jian Liu, Yan Wang, Yingying Chen, Bo Yuan,
Proceedings of the European Conference on Computer Vision (Springer ECCV 2022) (Acceptance rate: 28%).
Audio-domain Position-independent Backdoor Attack via Subsecond Triggers,
Cong Shi, Tianfang Zhang, Zhuohang Li, Huy Phan, Tianming Zhao, Yan Wang, Jian Liu, Bo Yuan, Yingying Chen,
Proceedings of the 28th Annual International Conference On Mobile Computing And Networking (ACM MobiCom 2022) (Acceptance rate: 17.8%).
Defending against Thru-barrier Stealthy Voice Attacks via Cross-Domain Sensing on Phoneme Sounds,
Cong Shi, Tianming Zhao, Wenjin Zhang, Ahmed Tanvir Mahdad, Zhengkun Ye, Yan Wang, Nitesh Saxena and Yingying Chen,
Proceedings of the 42nd IEEE International Conference on Distributed Computing Systems (IEEE ICDCS 2022) (Acceptance rate: 19.9%).
Robust Detection of Machine-induced Audio Attacks in Intelligent Audio Systems with Microphone Array,
Zhuohang Li, Cong Shi, Tianfang Zhang, Yi Xie, Jian Liu, Bo Yuan, Yingying Chen,
Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (ACM CCS 2021).
Face-Mic: Inferring Live Speech and Speaker Identity via Subtle Facial Dynamics Captured by AR/VR Motion Sensors,
Cong Shi, Xiangyu Xu, Tianfang Zhang, Payton R. Walker, Yi Wu, Jian Liu, Nitesh Saxena, Yingying Chen, Jiadi Yu,
Proceedings of the Annual International Conference on Mobile Computing and Networking (ACM MobiCom 2021) (Acceptance rate: 17.4%).
Environment-independent In-baggage Object Identification Using WiFi Signals,
Cong Shi, Tianming Zhao, Yucheng Xie, Tianfang Zhang, Yan Wang, Xiaonan Guo, Yingying Chen,
Proceedings of the IEEE International Conference on Mobile Ad-Hoc and Smart Systems (IEEE MASS 2021).
Enabling Fast and Universal Audio Adversarial Attack Using Generative Model,
Yi Xie, Zhuohang Li, Cong Shi, Jian Liu, Yingying Chen, Bo Yuan,
Proceedings of the AAAI Conference on Artificial Intelligence (AAAI 2021). (Acceptance rate: 1692/7911=21.3%)
Towards Environment-independent Behavior-based User Authentication Using WiFi,
Cong Shi, Jian Liu, Nick Borodinov, Bruno Leao, Yingying Chen,
Proceedings of the 17th IEEE International Conference on Mobile Ad-Hoc and Smart Systems (IEEE MASS 2020).
WearID: Low-Effort Wearable-Assisted Authentication of Voice Commands via Cross-Domain Comparison without Training,
Cong Shi, Yan Wang, Yingying Chen, Nitesh Saxena, Chen Wang,
Proceedings of the 36th Annual Computer Security Applications Conference (ACSAC 2020). (Acceptance rate: 70/302=23.2%)
Mobile Device Usage Recommendation based on User Context Inference Using Embedded Sensors,
Cong Shi, Xiaonan Guo, Ting Yu, Yingying Chen, and Jian Liu,
Proceedings of International Conference on Computer Communications and Networks (IEEE ICCCN).
Real-time, Universal, and Robust Adversarial Attacks Against Speaker Recognition Systems,
Yi Xie, Cong Shi, Zhuohang Li, Jian Liu, Yingying Chen, Bo Yuan,
Proceedings of the 45th International Conference on Acoustics, Speech, and Signal Processing (ICASSP 2020).
Practical Adversarial Attacks Against Speaker Recognition Systems,
Zhuohang Li, Cong Shi, Yi Xie, Jian Liu, Bo Yuan, Yingying Chen,
Proceedings of the 21st International Workshop on Mobile Computing Systems and Applications (ACM HotMobile 2020). (Acceptance rate: 16/48=33.3%)
CardioCam: Leveraging Camera on Mobile Devices to Verify Users While Their Heart is Pumping,
Jian Liu, Cong Shi, Yingying Chen, Hongbo Liu, Marco Gruteser,
Proceedings of the 17th ACM International Conference on Mobile Systems, Applications, and Services (ACM MobiSys 2019). (Acceptance rate: 40/172 = 23.2%)
Device-free Personalized Fitness Assistant Using WiFi,
Xiaonan Guo, Jian Liu, Cong Shi, Hongbo Liu, Yingying Chen, Mooi Choo Chuah,
Jin PACM on Interactive, Mobile, Wearable, and Ubiquitous Computing, Volume 2, Issue 4, Pages 1-23, 2018. (presented at UbiComp 2019).
WiFi-Enabled Smart Human Dynamics Monitoring,
Xiaonan Guo, Bo Liu, Cong Shi, Hongbo Liu, Yingying Chen, Mooi Choo Chuah,
Proceedings of the 15th ACM Conference on Embedded Networked Sensor Systems (ACM SenSys 2017). (Acceptance rate: 26/151 = 17.2%)
Secret Key Distribution Leveraging Color Shift Over Visible Light Channel,
Hongbo Liu, Bo Liu, Cong Shi, Yingying Chen,
Proceedings of IEEE Conference on Communications and Network Security (IEEE CNS 2017).
Smart User Authentication through Actuation of Daily Activities Leveraging WiFi-enabled IoT
Cong Shi, Jian Liu, Hongbo Liu, Yingying Chen,
Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing (ACM MobiHoc 2017). (Acceptance rate: 27/179 = 15.1%)
Journal Papers & Magazine Articles
RF Domain Backdoor Attack on Signal Classification Via Stealthy Trigger,
Zijie Tang, Tianming Zhao, Tianfang Zhang, Huy Phan, Yan Wang, Cong Shi, Bo Yuan, Yingying Chen,
IEEE Transactions on Mobile Computing (IEEE TMC), 2024.
Simultaneous Monitoring of Multiple People's Vital Sign Leveraging a Single Phased-MIMO Radar,
Zhaoyi Xu, Cong Shi, Tianfang Zhang, Shuping Li, Yichao Yuan, Chung-Tse Michael Wu, Yingying Chen, Athina Petropulu,
IEEE Journal of Electromagnetics, RF, and Microwaves in Medicine and Biology (IEEE JERM), 2022.
mPose: Environment- and Subject-Agnostic 3D Skeleton Posture Reconstruction Leveraging a Single mmWave Device,
Cong Shi, Li Lu, Jian Liu, Yan Wang, Yingying Chen, Jiadi Yu,
Elsevier Smart Health, 2021.
Authentication of Voice Commands on Voice Assistance Systems Leveraging Vibrations on Wearables,
Cong Shi, Yan Wang, Yingying Chen, Nitesh Saxena,
IEEE Security & Privacy Magazine (IEEE S&P), 2021.
Enabling Secret Key Distribution Over Screen-to-Camera Channel Leveraging Color Shift Property,
Hongbo Liu, Cong Shi, Yingying Chen,
IEEE Transactions on Mobile Computing (IEEE TMC), 2021. (To appear)
WiFi-enabled User Authentication through Deep Learning in Daily Activities,
Cong Shi, Jian Liu, Hongbo Liu, Yingying Chen,
ACM Transactions on Internet of Things (ACM TIOT),
Volume 2, Issue 2, No. 13, 2021.
Real-time, Robust and Adaptive Universal Adversarial Attacks Against Speaker Recognition Systems,
Yi Xie, Zhuohang Li, Cong Shi, Jian Liu, Yingying Chen, Bo Yuan,
Journal of Signal Processing Systems (Springer JSPS),
2021. (To appear)
Device-free Personalized Fitness Assistant Using WiFi,
Xiaonan Guo, Jian Liu, Cong Shi, Hongbo Liu, Yingying Chen, Mooi Choo Chuah,
PACM on Interactive, Mobile, Wearable, and Ubiquitous Computing (IMWUT),
Volume 2, Issue 4, No. 165, 2018.
Improvement of the depth resolution in depth-resolved wavenumber-scanning interferometry using multiple uncorrelated wavenumber bands,
Jinxiong Xu, Yufei Liu, Bo Dong, Yulei Bai, Linlin Hu, Cong Shi, Zhuoming Xu, Yanzhou Zhou,
Applied Optics, Volume 52, number 20, pages 4890-4897.
Refereed Workshop Papers, Posters, and Demos
Poster: Personalized Health Monitoring via Vital Sign Measurements Leveraging Motion Sensors on AR/VR Headsets,
TTianfang Zhang, Cong Shi, Tianming Zhao, Zhengkun Ye, Payton Walker, Nitesh Saxena, Yan Wang, Yingying Chen,
Proceedings of the 20th ACM International Conference on Mobile Systems, Applications, and Services (MobiSys),
Poster: Continuous Blood Pressure Monitoring Using Low-cost Motion Sensors on AR/VR Headsets,
Tianming Zhao, Zhengkun Ye, Tianfang Zhang, Cong Shi, Ahmed Tanvir Mahdad, Yan Wang, Yingying Chen, Nitesh Saxena,
Proceedings of the 20th ACM International Conference on Mobile Systems, Applications, and Services (MobiSys),
Poster: Speech Privacy Attack via Vibrations from Room Objects Leveraging a Phased-MIMO Radar,
Cong Shi, Tianfang Zhang, Zhaoyi Xu, Shuping Li, Yichao Yuan, Athina Petropulu, Chung Tse Michael Wu, Yingying Chen,
Proceedings of the 20th ACM International Conference on Mobile Systems, Applications, and Services (MobiSys),
Demo: Device-free Activity Monitoring Through Real-time Analysis on Prevalent WiFi Signals,
Cong Shi, Justin Esposito, Sachin Mathew, Amit Patel, Rishika Sakhuja, Jian Liu, Yingying Chen,
Proceedings of the IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN),
Multiresolution mutual information method for social network entity resolution,
Cong Shi, and Rong Duan,
Proceedings of the IEEE International Conference on Data Mining Workshop (ICDMW),
